Fake apps are the latest evolution of brand impersonation, and they’re proving just as dangerous as phishing sites. Fraudsters clone legitimate mobile apps, publish them on official app stores, and trick users into entering credentials — which are then reused in the real app before anyone notices. Given that over 60% of web traffic is now mobile, this form of phishing-driven credential reuse has become one of the top blind spots in mobile fraud defense. Yet most mobile security tools can’t detect it — because they don’t know where those credentials came from.
How Fake Apps Enable Credential Reuse
Mobile app account takeover occurs when an attacker gains unauthorized access to a user’s account through the mobile app interface – usually by leveraging stolen credentials. These credentials are often collected through phishing, credential stuffing, or breaches in other channels and then reused to access accounts in the mobile environment.
Attackers don’t just send phishing links anymore. Today, they build full-blown fake apps and submit them to app stores, often using cloned UI and stolen branding. Users download them thinking they’re real and submit login credentials that are immediately harvested. From there, those credentials are reused in the real mobile app, enabling stealth ATO without triggering alerts.
Why Mobile App Credential Reuse Is a Growing Threat
Mobile apps now account for over 55% of digital engagement globally (Statista, 2024). For fraudsters, this means a larger, more fragmented attack surface to exploit, especially when phishing-based attacks span web, social, and app store ecosystems.
This fragmentation is particularly dangerous in high-value industries:
- Banking apps give attackers direct access to funds and account data.
- Retail and e-commerce apps often store loyalty points, saved cards, and one-click purchasing capabilities – ideal for fraud monetization.
- Travel and airline apps allow for itinerary changes, miles redemption, and personal data access, leading to both financial loss and customer churn.
The most common mobile ATO pathways include:
- Phishing sites optimized for mobile that trick users into submitting credentials
- Brand impersonation via fake app listings or social campaigns
- Credential reuse from previously phished or leaked logins
- Automated credential stuffing attacks targeting mobile login APIs
Given the overlapping threats, detecting and stop credential reuse attacks where they converge – at the point of login in the legitimate mobile app – is arguably the only scalable solution. Embracing that reality means first moving away from outdated approaches.
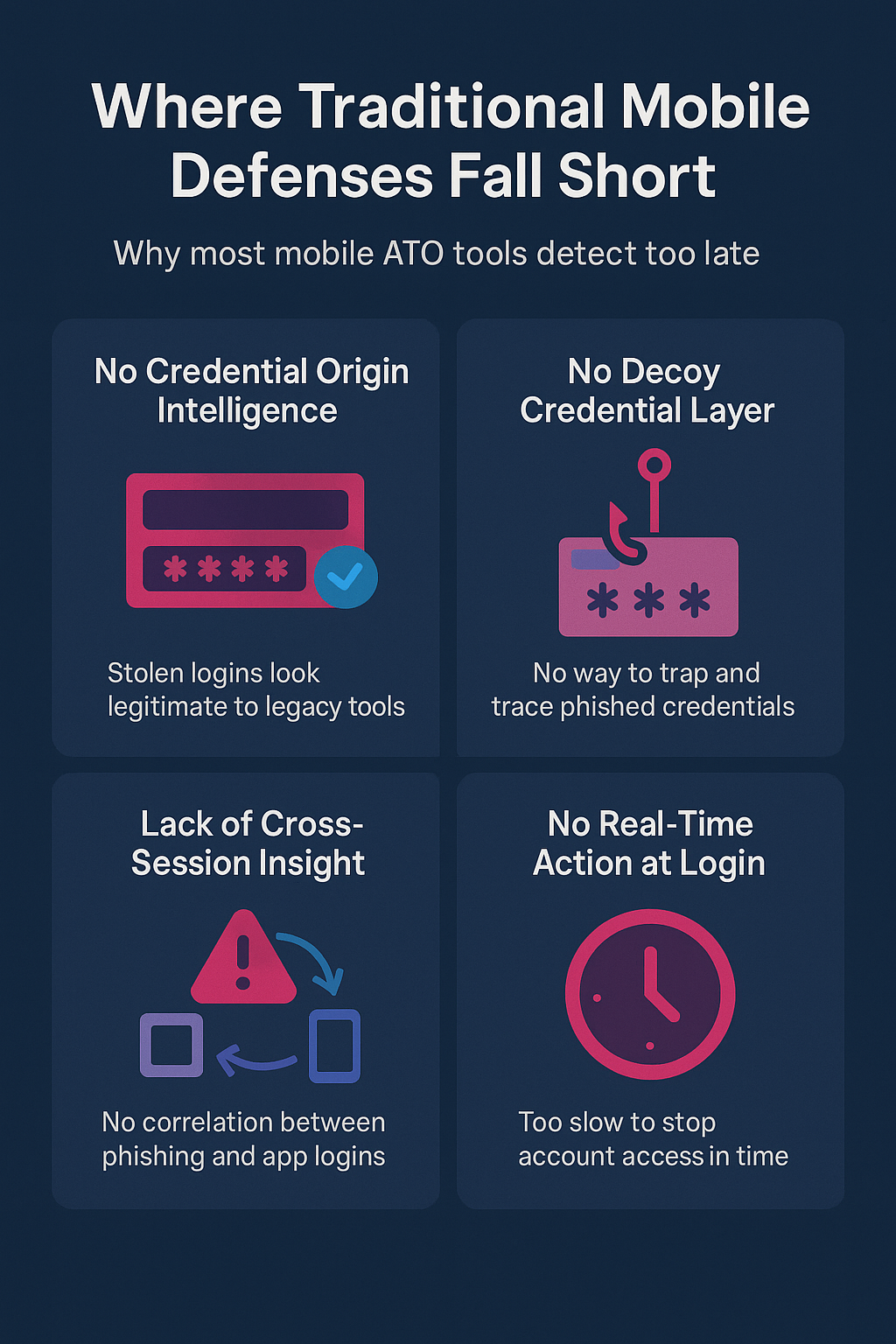
Where Traditional Mobile Defenses Fall Short
Many fraud and anti-phishing tools focus on post-login activity or in-app behavior, but they miss the root cause. Today’s attacks often start upstream, when users are tricked into entering credentials inside fake mobile apps impersonating your brand. By the time attackers reuse those logins in your real app, it’s too late to stop them, unless you connect the dots earlier.
1. Blind to App Store Impersonation
Traditional mobile defenses don’t monitor app stores or fake app listings, allowing fraudsters to publish clones that harvest credentials undetected.
2. Lack of Credential Origin Intelligence
Most anti-fraud or ATO protection tools don’t track where stolen credentials come from. That means attackers using valid credentials in your real app often go undetected.
3. No Decoy Credential Layer
With decoy credential injection, it’s possible to deceive credential harvesters into exposing attack device attributes and locking themselves out, while identifying stolen data.
4. Incomplete Cross-Session Insight
Mobile sessions may look clean. But without correlation to prior phishing events, or low-reputation referral patterns, the signal is lost.
5. No Real-Time Action at Login
Even when an anomaly is flagged, there’s often no capability to intervene before account access is granted.
Most mobile fraud defenses fail to connect phishing, credential theft, and app login misuse, leaving threat actors free to exploit compromised logins in real time.
Memcyco Detects App Impersonation Before Damage Is Done
Fake apps don’t just appear out of nowhere, they leave digital fingerprints. Memcyco monitors official app stores, social media, and referral patterns to detect unauthorized app listings, brand elements or naming schemes that mimic your legitimate app, and spoofed download campaigns impersonating your brand. This early warning lets you act before users are tricked, and before stolen credentials are used in your real app.
How Memcyco Stops Credential Misuse from Fake Apps and Phishing Attacks
Whether credentials are phished through fake apps, spoofed websites, or malicious ads, Memcyco detects their misuse the moment attackers try to use them in the real app.
Memcyco’s agentless, real-time solution detects and mitigates credential misuse in real-time across mobile and web by detecting session anomalies, suspicious referrals, and decoy credential replay patterns.
Real-Time Credential Misuse Detection
- Detects stolen credentials replayed in legitimate apps, even if harvested through fake apps or spoofed mobile sites
- Flags login attempts from devices that interacted with known impersonation campaigns or phishing infrastructure
- Surfaces correlated signals across sessions, devices, and credential origin channels
Related: How to Detect and Stop Reverse Proxy Phishing Attacks in Real-Time
Decoy Credential Injection
- Replaces credentials entered on phishing sites or fake mobile apps with decoys
- Detects decoy replay attempts inside real mobile login flows
- Reveals compromised sessions tied to specific devices or campaigns
Device Fingerprinting
- Tracks login behavior across known and unknown devices
- Flags reused or suspicious device fingerprints, even in clean sessions
Backend Login Telemetry
- Analyzes login attempts in real time via API integrations
- Detects credential stuffing, brute force, and credential anomalies without SDKs
All of this happens invisibly and seamlessly with no app changes or impact on user experience. In other words, Memcyco delivers high-fidelity login signals, enabling preemptive intervention options, without requiring in-app instrumentation.
Read more: How Browser-Level Signals Help Prevent Credential Stuffing Attacks
Why Memcyco Has Leading Analysts Paying Attention
Memcyco was recognized in Datos Insight’s Q1 2025 Fintech Spotlight for its innovative approach to phishing and ATO prevention.
Book a demo to see how Memcyco delivers real-time protection for mobile and web channels, saving global enterprises tens of millions annually in incident-related costs.
FAQs About Credential Reuse Attacks
How does phishing lead to mobile ATO?
Phishing sites harvest credentials from users. Attackers then reuse those credentials inside real apps to gain access, often before anyone notices.
How can Memcyco detect phishing-driven mobile ATO?
Memcyco flags login attempts from suspicious devices, detects replay of decoy credentials, and identifies referrals from phishing origins, helping stop fraud before login succeeds.
Does Memcyco require changes to the mobile app?
No. Memcyco operates entirely via backend API monitoring. There’s no SDK, no in-app code, and no UX disruption.
What are best practices for preventing credential reuse?
- Inject decoy credentials to trap phishers
- Track credential replay across sessions
- Flag device fingerprint anomalies
- Monitor backend login telemetry
- Intervene before granting access
Does this help with compliance?
Yes. Demonstrating real-time fraud detection at login and credential misuse prevention supports compliance with emerging digital identity and data protection regulations. It also provides a foundation for conducting internal credential reuse audits, helping teams assess vulnerabilities and strengthen identity controls.